6.65 m mobile phone users are expanding worldwide every year. Mobile app security with technical advancement becomes essential for start-ups to be in the competitive market.
Mobile apps are the biggest revenue generators and at the same time, they face security challenges and cyber threats more than anything.
87% of mobile phone users spend their most of the time on mobile apps.
Many dedicated developers tirelessly bring brilliant ideas to life and craft an app that will revolutionize the way people order pizza or find the perfect dog-walking companion.
With carefully designing every pixel and coding every line, you can almost taste the glory and success on the horizon. But hold your horses! Before you launch your app into the wild, there’s a vital aspect you must address- Security.
Now you might be thinking- Why should I worry about security?
Ah, my dear reader, it’s time for a security check. Just like a juicy watermelon on a hot summer day. Your app is bound to attract some unsavoury characters that see it as a golden opportunity. To exploit vulnerabilities and get their hand on valuable user data.
They lurk in the shadows armed with an arsenal of hacking tools and nefarious intentions.
But fear not! We are here to arm you with the knowledge and equip you with the best practices that will help you in protecting your user data. Think of us as your trusty cyber security and let’s explore the practices by which you can protect your user data.
So, without further ado, let’s get started!
“The only truly secure system is one that is powered off, cast in a block of concrete, and sealed in a lead-lined room with armed guards.” – Gene Spafford
Significance of Mobile App Security in Mobile App Development
“Security is not a product, but a process.” – Bruce Schneier
When it comes to mobile app security, one in four mobile apps contains at least one high-risk security flaw. With 3.8 Bn mobile phone users around the globe, 25% of 2 m applications available on the Google Play store include a security flaw. Whether it’s mobile banking app development or any other mobile app development, this process should be in expert hands.
Now you are wondering why mobile app security becomes this big issue but first, let’s talk about what is mobile app security.
What is mobile app security?
Mobile apps security refers to the measures and practices employed to protect mobile applications from unauthorized access, data breaches, and malicious activities.
It encompasses various techniques, protocols, API security, and other best practices aimed at ensuring the confidentiality, integrity, and availability of user data.
Plus, the overall security of the application itself.
Moreover, it involves safeguarding the app’s infrastructure, user data, and the interactions between the app and its users. It includes protecting against threats such as:
- Malware
- Data leakage
- Unauthorized access
- Social engineering attacks
- Other vulnerabilities
These can compromise the security and privacy of user information. Now, let’s talk about the importance of mobile app security.
Importance of mobile app security
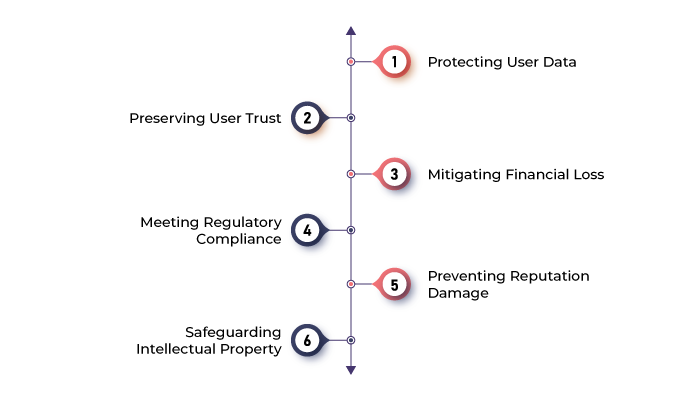
We all know how important app security is in today’s digital landscape. Here are several key reasons why mobile app security is of paramount importance:
Protecting User Data
The mobile app often handles sensitive user information, including personal details, financial data, and confidential communications.
With effective app security measures safeguard this data from unauthorized access, ensuring privacy and protecting users from identity theft, fraud, and other malicious activities.
Preserving User Trust
Every user wants their personal information in safe hands. By prioritizing mobile app security, developers demonstrate their commitment to user privacy and build trust with their audience.
By developing PCI DSS-compliant fintech mobile app, user data get secured from malicious activity.
This trust is crucial for maintaining a loyal user base and fostering long-term relationships with customers.
Mitigating financial loss
With fintech app development data breaches and security incidents can have severe financial implications for businesses. The cost associated with remediation, legal repercussions, regulatory fines, and damage to reputation can be significant.
So investing in robust app security measures helps minimizes the risk of data breaches, reducing potential financial losses.
Meeting regulatory compliance
Many industries are subject to specific regulations and standards governing the protection of user data.
Mobile app security plays a major role in ensuring compliance with these regulations such as the general data protection regulation (GDPR) or the payment card industry data security standard ( PCI DSS). Failing to comply with such regulations can result in legal consequences and reputation damage.
Preventing reputation damage
Data breaches and security incidents can severely harm a company’s reputation. News of compromised user data spreads quickly and erodes trust in the app and the organization behind it.
This is why secure mobile app helps users to protect the brand reputation, maintaining a positive image in the eyes of users and the public.
Safeguarding intellectual property
Mobile apps often incorporate proprietary algorithms, trade secrets, or unique functionalities that contribute to a company’s competitive advantage.
Inadequate security measures can expose these valuable assets to theft or unauthorized use, compromising a business’s intellectual property rights. Let’s look at mobile app security threats that demand attention in the next section.
Mobile App Security Threats That Demand Attention
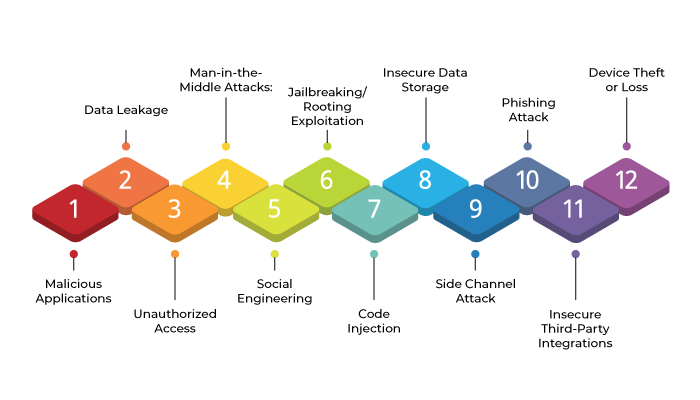
Mobile app security faces a range of mobile app security threats that target vulnerabilities in the application itself, user interactions, and the overall mobile ecosystem.
Understanding these threats is essential for implementing effective security measures.
Here are some common mobile app security threats:
Malicious applications
Malware and malicious apps pose a significant threat to mobile devices. These apps are designed to exploit vulnerabilities, gain unauthorized access to sensitive information, or disrupt device functionality.
Data leakage
Apps that handle sensitive user data may maliciously leak that data. This can occur due to poor data handling practices, insufficient encryption, or insecure transmission channels.
Unauthorized access
Attackers may attempt to gain access to user accounts, either through exploiting weak authentication mechanisms or leveraging stolen credentials.
Plus, conduction brute force attacks.
Man-in-the-middle (MITM) Attacks:
In a MitM attack, an attacker intercepts communication between an app and its backend servers or between two users. This allows them to eavesdrop, modify, or inject malicious content into the communication.
Social engineering
Social engineering involves manipulating users into performing actions that compromise their own security. This can include tricking users into revealing sensitive information, clicking on malicious links, or downloading compromised apps.
Jailbreaking/ Rooting exploitation
Jailbreaking (iOS) or rooting (Android) devices can bypass security measures and grant attackers deeper access to the operating system, potentially compromising app security.
Code Injection
Attackers may inject malicious code into an app to exploit vulnerabilities or gain unauthorized access to data or system resources.
Insecure data storage
Weak or vulnerable data storage leads to practices that can leave sensitive information for unauthorized access. This includes storing data in plain text, using weak encryption algorithms, or storing data in easily accessible locations.
Side channel attack
Side-channel attacks exploit information leaked during the execution of an app, such as timing variations, power consumption, or electromagnetic emissions to infer sensitive data.
Phishing attack
Attackers may attempt to deceive users into revealing their credentials or sensitive information by mimicking legitimate app interfaces or sending deceptive messages.
Insecure third-party integrations
Vulnerabilities in third-party libraries, software development kits (SDKs), or application programming interfaces (APIs) can introduce security weaknesses into mobile apps. Plus, not taking care of mobile app security standards while starting custom mobile app development.
This is the most common reason for an attacker to exploit them for unauthorized access or data leakage.
Device Theft or loss
When a device is stolen or lost, unauthorized individuals may gain physical access to the app and its data. Without adequate security measures, this can lead to data breaches and unauthorized usage.
To mitigate these threats, mobile app developers must implement robust mobile app security checklist such as secure authentication mechanisms, encryption, and regular security assessments.
On-going monitoring and updating of security protocols are also crucial to address emerging mobile app security threats and vulnerabilities.
How Can I Protect Private Info Of Smartphones?
We have already discussed the threats now for mobile app security measures and proper precautions when you log into iPhone or Android apps. The following mobile app security testing tools or measures can increase the odds of staying safe.
| Set Strong Passcode or passwords
| Use a strong, unique passcode or password to secure your device. Avoid easy-to-guess patterns or codes like “1234” or “0000”.
|
| Enable Biometric Authentication
| Take advantage of biometric authentication options like fingerprint or facial recognition to add an extra layer of security to unlock your device.
|
| Keep your operating system and apps updated
| Regularly update your smartphone’s operating system and applications. Updates often include security patches that address vulnerabilities and protect against emerging threats.
|
| Be cautious of app permissions
| Pay attention to the permissions requested by apps during installation. Only grant necessary permissions and be mindful of apps requesting access to sensitive data or features.
|
| Install apps from trusted sources
| Stick to official app stores like Google Play Store or Apple App Store to download and install apps. These platforms have security measures in place to minimize the risk of malicious apps.
|
| Use a mobile security app
| Consider installing reputable mobile security apps that provide features like malware scanning, anti-theft protection, and safe browsing.
|
| Be wary of phishing attempts
| Be cautious of unsolicited emails, text messages, or calls asking for personal information. Avoid clicking on them.
|
| Secure WI-FI connections
| When connecting to Wi-Fi networks, use encrypted networks whenever possible. Avoid accessing sensitive information or making financial transactions on public or unsecured networks.
|
| Encrypt device storage
| Enable encryption on your device storage to protect your data if your device falls into the wrong hands. |
Conclusion
As technology continues to advance, mobile app security will remain a crucial area of focus.
By staying proactive, investing in security measures, and fostering a security-centric culture, we ensure the protection of private information, maintain the integrity of mobile apps, and create a safer digital environment for users worldwide.
If you want to prioritize mobile app security to safeguard your data and empower a secure mobile app ecosystem feel free to contact us.
FAQs
Common mobile app security threats include malicious applications, data leakage, unauthorized access, man-in-the-middle attacks, social engineering, jailbreaking/rooting exploitation, code injection, insecure data storage, side-channel attacks, phishing attacks, insecure third-party integrations, and device theft or loss.
To protect your mobile app from malware, follow these best practices:
- Regularly update the app with security patches.
- Use secure coding practices and conduct code reviews.
- Implement strong authentication mechanisms.
- Encrypt sensitive user data.
To secure user data in your mobile app:
- Implement strong encryption techniques for data at rest and in transit.
- Use secure communication protocols, such as SSL/TLS.
- Follow secure coding practices to avoid vulnerabilities.
- Store sensitive data securely, such as using encryption and access controls.
To ensure secure authentication in your mobile app:
- Implement strong password policies and enforce password complexity.
- Consider implementing two-factor authentication (2FA).
- Utilize biometric authentication methods, such as fingerprint or facial recognition.
- Use secure authentication protocols like OAuth and Single Sign-On (SSO).
If your mobile app experiences a data breach, take immediate action:
- Notify affected users and provide clear communication.
- Investigate the breach to determine the extent and cause.
- Address the vulnerability or security flaw that led to the breach.
- Engage with cybersecurity professionals or incident response teams.
- Comply with legal and regulatory requirements.
To stay updated on mobile app security best practices:
- Follow reputable security blogs, industry publications, and forums.
- Attend conferences, webinars, and workshops related to mobile app security.
- Join relevant professional networks and communities.
- Engage with cybersecurity experts and participate in knowledge-sharing events.
Yes, several industry regulations and standards address mobile app security. Examples include the General Data Protection Regulation (GDPR) for data protection and privacy, the Payment Card Industry Data Security Standard (PCI DSS) for handling payment card data.
Yes, performing security testing for your mobile app is crucial. It helps identify vulnerabilities, weaknesses, and potential entry points for attackers. Security testing includes techniques like penetration testing, code review, and security assessments to ensure the app’s resilience against threats.
To create a security-centric culture:
- Provide regular security training and awareness programs to employees.
- Encourage reporting of security incidents and concerns.

Udai Singh is a senior content writer with over 6 years of experience in creating content for FinTech, eWallet, EdTech, and App Development. He is an expert in simplifying complex concepts and creating engaging content that resonates with the audience.
Table of Contents












No Comments
Comments are closed.