The user is the ultimate authority!
This is a fundamental lesson to apply when planning a mobile application built for the masses. One of the core responsibilities of a business is to ensure that its users’ data stays secure.
This is not only the concern of the user, but the governing bodies are also interested and want to make sure that your application keeps the data intact, which is why regulations and compliance are set in place. SOC 2 is one of the core compliance requirements.
However, it often becomes a complex task for the application developers to build an SOC 2 Compliant system. That is because there’s a complete process that one has to follow, and the process is certainly complicated.
In this post, let us understand what exactly SOC 2 compliance is and what the requirements an app has to meet, and why it is crucial. So if you’re struggling with meeting SOC 2 requirements or planning to build an app, make sure you read this one till the end.
What is SOC 2 Compliance?
SOC 2 compliance is one of the most important requirements for any application that interacts with, collects, or manages user data. Just like fintech compliance and regulations, or for any other industry, the SOC 2 also focuses on making the application a trustworthy and secure place for the user’s data.
The framework is based on the American Institute of Certified Public Accountants’ five trust services criteria, which allow an organization to be transparent about its data policies and ensure that an application is safeguarding the data. The entire focus is on user security and privacy, which makes compliance even more important.
System and Organization Controls, commonly referred to as SOC2, is a compliance report that helps a business evaluate the security risks and practices of the vendors that it plans to get involved with.
The idea is to understand the way a company functions and whether its practices align with your risk tolerance or not.
By making third-party collaborations safe and secure, SOC2 compliance can not only make an organization more secure but also help them identify and mitigate potential risks, simply by identifying the gaps through SOC2.
SOC 2 Trust Services Criteria (TSC)
The entire SOC2 compliance is based on the Trust Services Criteria as defined by the AICPA. These service criteria focus on 5 major factors that determine whether the application you plan to launch is safe for user data and aligns with safety compliance or not.
The TSC includes the following points:
- Security: Focuses on protecting the app’s system from unauthorized access or any type of data breach.
- Availability: Helps in ensuring that the app features are available as promised to the users.
- Process Integrity: Ensures that data is being processed accurately, timely manner, and that the integrity of the data is maintained.
- Confidentiality: This criterion focuses on maintaining the confidentiality of the data, saving it from uninvited disclosure.
- Privacy: The latest TSC states that all personally identifiable information is collected, kept, and used privately.
While this is just an overview of the TSCs, you might have gotten an idea of why the compliance is highly regarded for user data privacy. When these criteria are met and implemented properly, it becomes easy for the app to show compliance with the SOC2.
However, it is not that simple. There is a complete checklist that needs to be followed to ensure that the application complies with SOC2. What are these points you ask? Check out the next section!
SOC 2 Implementation Checklist – Steps to Get SOC 2 Compliance
Implementing SOC2 into your application requires multiple factors to be considered, which is why several applications and businesses should follow to clear the audit.
The first thing to do is to complete a pre-assessment of the app to understand existing security practices and where it stands. Based on the gaps that are identified, a set of policies is implemented to meet the TSCs.
When the implementation is completed, you are left with a solid security framework that is compliant with the SOC 2 regulations. However, it is not that simple.
Here’s a complete checklist you can follow to gain SOC 2 compliance:
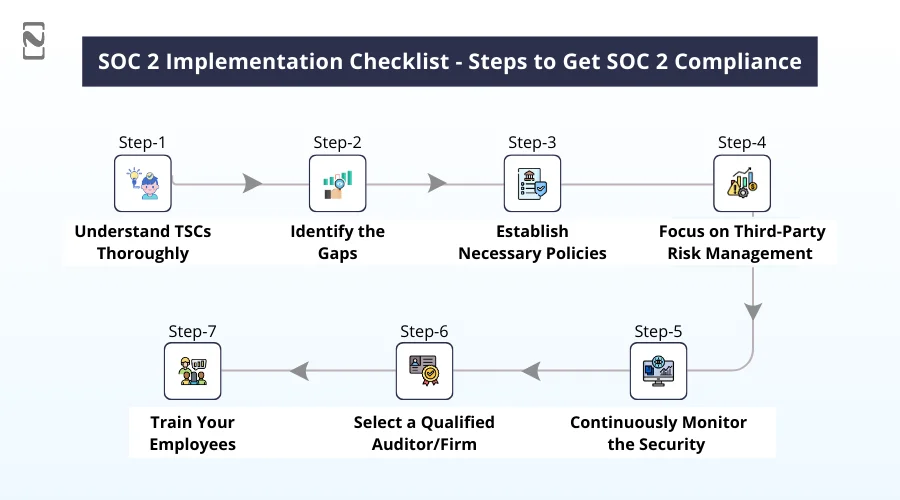
► Understand TSCs Thoroughly
The Trust Services Criteria is the key player in implementing SOC 2 compliance. Hence, you need to start by breaking them down. You will need all types of resources, from technology to human resources, to understand the processes, data, and systems that are currently in place.
► Identify the Gaps
Based on the TSC, start assessing your existing systems to identify the issues. This step requires you to see through the current functionalities of the system and put the current system to test with respect to the 5 criteria that we have discussed earlier.
The assessment will automatically highlight the gaps that are present in the application’s security and risk management capabilities.
► Establish Necessary Policies
After you have identified the issues or gaps in the security of your application, it is time to analyse them thoroughly. Based on this analysis, you need to develop a few policies on how the app collects, manages, and stores the data of users.
You also need to analyze what new features can be implemented into the application. Keep your focus on the access control, security controls, and data handling of your app, as generally these are the core problems where your application suffers.
► Focus on Third-Party Risk Management
Once the internal assessment of the application’s security system is done, it is time to focus on the third-party risk management. Whenever a third party is involved in the functioning of any feature, the chances are that the data will either be at risk or will be misused.
In order to ensure that the solution you have is able to manage these third-party risks and has a higher risk tolerance, it is critical to identify and resolve issues so that compliance can be earned.
► Continuously Monitor the Security
Before going directly for compliance, take your time and monitor the current security posture of the application. It is crucial to be sure of what you are planning to enter into. Identify any flaws or inconsistencies in the security policies that you have deployed in the previous steps.
Refine the process to ensure that there are no gaps left. Repeat this process thoroughly before applying for the SOC 2 compliance certification.
► Select a Qualified Auditor/Firm
One of the key things to keep in mind is that you only need a professional to validate your application. Find a qualified firm that can build a SOC 2 report based on your current security posture and performance.
This SOC2 report defines how your application manages data security and offers the user a safer space to use. As per the AICPA, you should only allow a licensed auditor to examine your application.
► Train Your Employees
Lastly, you need to train your employees to be more compliant with the practices and systems that are required to meet the SOC 2 requirements. You see, while all these steps will help you get the compliance approved, you also need to maintain the security level to keep it intact.
Your employees can help you ensure that the application is taken care of in terms of mitigating risks, identifying loopholes, and more.
With the help of this checklist, you not only make your application ready for SOC2 compliance but also strengthen the overall security posture of your organization, which is a plus in today’s scenario.
Benefits of SOC 2 Compliance for Your App
As you might have understood by now, the SOC 2 is a compliance that actually ensures that the user data is being used properly and the application is able to handle the shared information properly.
More importantly, it helps in establishing user-app trust as knowing that the company is able to manage the data shared responsibly.
When your application is SOC 2 certified, it brings along several benefits for you. These benefits include:
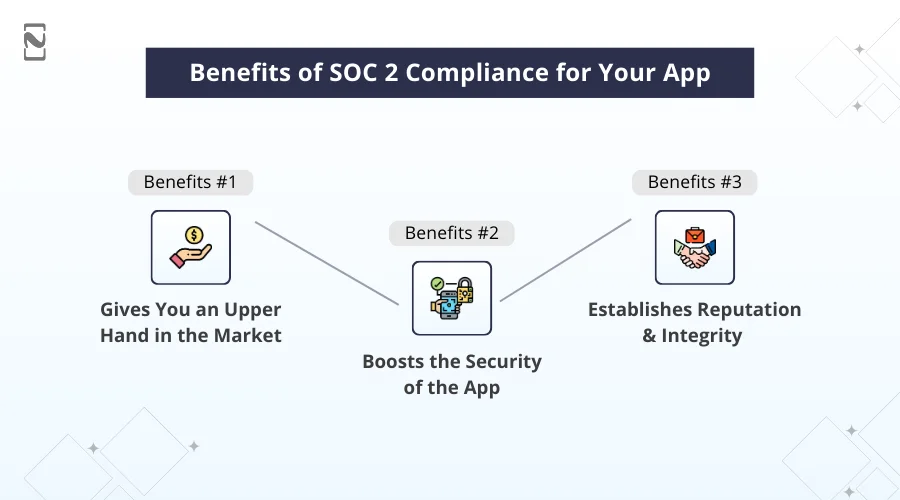
♦ Gives You an Upper Hand in the Market
The current generation is well aware of the data policies and the crucial nature of data privacy while being online.
Hence, when your application offers them security in terms of compliance, they are automatically more inclined to use your application than any other in the same niche.
Getting your application SOC 2 compliant makes it more and more desirable for the user, giving you an upper hand in the market.
♦ Boosts the Security of the App
When we talk about mobile app security, the first thing that comes to mind is ways to unlock it or keep things private when using it. However, what many users do not realize is that the data is not only at risk when the app is being used.
In fact, it is always at risk if the app is unable to manage or store it properly. The SOC 2 Compliant application gives the user enough confidence to freely share their data, as it boosts the overall security of the application.
♦ Establishes Reputation and Integrity
Unlike any other compliance that is mandatory for the application, the SOC2 compliance is a huge deal in the market. Offering your users the flexibility to choose security puts your application on a higher pedestal, making it more reliable and reputable.
Not to mention, the integrity of the data stored on the app server is certainly maintained, as it shows directly in the SOC2 audit report. The benefits are unreal.
Other than these benefits, the sheer fact that an SOC 2 Compliant company is preferred over an option that does not hold the compliance certificate in itself puts you ahead in the market. Hence, spending on SOC2 compliance is certainly a worthwhile investment.
Conclusion
With cybersecurity being a central point of concern for many users, making your application’s security iron-clad should always be your priority, and with the help of SOC 2 compliance, you can achieve that quite easily.
Not only does compliance help you stay on top of your app’s security, but it also helps a third party identify your risk tolerance, making collaboration simple and secure.
It is as crucial as adding a security feature to your application. Hence, you need to consider the compliance certificate and opt for it when building your application.
With that said, we have reached the end of this blog. Hope this post gives you a proper introduction to SOC 2 compliance. For further details, you can connect with our experts.
FAQs

Niketan Sharma, CTO, Nimble AppGenie, is a tech enthusiast with more than a decade of experience in delivering high-value solutions that allow a brand to penetrate the market easily. With a strong hold on mobile app development, he is actively working to help businesses identify the potential of digital transformation by sharing insightful statistics, guides & blogs.
Table of Contents



No Comments
Comments are closed.